With the recent announcements of the availability of SSO for Dropbox, I wanted to see if it was possible to configure this against our ADFS 2.0 installation. Read on to see how I did it.
Overview
At Blue Rooster, our designers primarily use Macs, and Dropbox is a heavily used utility for sharing and collaborating on large design files. We have a business account, and have been utilizing Dropbox native accounts with our company email addresses as our account names. Managing these accounts has all of the traditional problems with external systems – different passwords, removing people when they leave the company, etc.
With the recent announcements of Dropbox Single Sign On capabilities, I wanted to see if it was possible to further leverage our ADFS infrastructure to provide SSO integration with Dropbox. While they don’t list ADFS as a turn-key supported provider (vendors like Ping, OneLogin, etc. are supported), it is all just SAML 2.0 after all and should work. Turns out it was pretty easy, here are the steps I took.
Step 1 – Export your Token Signing Certificate
On the SSO help page for DropBox, it has the following paragraph about certificates and encryption:
- Your identity provider may ask if you want to sign the SAML assertion, the SAML response, or both. Dropbox requires the SAML response to be signed. You can choose signed or unsigned for the SAML assertion.
I scratched my head for a bit trying to grok this, but really all this means is that ADFS already signs its tokens (response), so you just need to export your token signing certificate from ADFS and provide that to Dropbox.
To export your certificate, follow the steps below (for Windows Server 2012):
- Open the ADFS management console and navigate to Services > Certificates.
- Click your Token Signing Certificate, and then click View Certificate.
- Click on the Details tab and click Copy to File.
- For the format, choose DER Encoded Binary. If prompted to export the private key, opt to not do that.
- Choose a file name and save it somewhere.
- Dropbox requires the cert in PEM format. You can easily convert the cert online. Go to https://www.sslshopper.com/ssl-converter.html. Provide your cert, choose DER/Binary for the source format, and Standard PEM for the target format, and then click Convert Certificate. It’ll ask you to download the file (with a .CRT extension).
- Change the file extension to .pem.
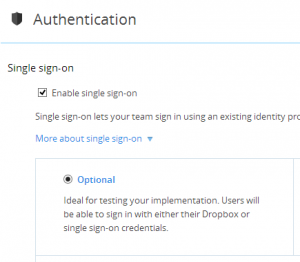
Step 2 – Enable SSO in Dropbox
Next step is to turn on SSO within Dropbox. Go to the Dropbox Admin console, and click on the Authentication link. Choose Enable SSO, and tick the Optional radio button.This is fantastic, because users can login totally normally while you test the SSO implementation.
You’ll see a text box for the Sign In Url. Dropbox SSO is a bit unintelligent, so you have to force Dropbox to tell ADFS who the request is coming from by specifying its identity in the url. Your url should look something like the following: https://adfs.contoso.com/adfs/ls/IdpInitiatedSignOn.aspx?logIntoRP=https://www.dropbox.com/saml_login.
For the certificate, upload your PEM file you created from Step 1 above.
Step 3 – Create the Relying Party in ADFS
The last step is to tell ADFS about Dropbox. Follow the steps below to create the RP:
- Open the ADFS Management Console. Click on Trust Relationships > Relying Party Trusts > Add Relying Party Trust.
- Choose to Enter the data about the relying party manually.
- For the name, type Dropbox or something similar. Click Next.
- Choose the ADFS profile with SAML 2.0 support.
- Skip configuring a certificate, you don’t need it.
- On the Configure URL screen, check the box for Enable support for the SAML 2.0 WebSSO protocol. In the url box, enter the following url: https://www.dropbox.com/saml_login.
- For the relying party trust identifier, enter the following url: https://www.dropbox.com/saml_login.
- Choose to permit all users to use this relying party.
- Next and Finish!
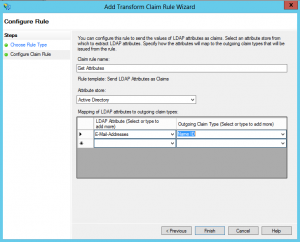
Finally, you need to add a claim rule/mapping to provide Dropbox with your user’s email address as the Name ID.
- Click on your newly created Relying Party Trust, and click Edit Claim Rules…
- Under the Issuance Transform Rules tab, click the Add Rule button.
- On the first page of the wizard, choose the Send LDAP Attributes as Claims option.
- On the next page, give your rule a name, something like Get Attributes.
- Choose Active Directory as the attribute store.
- On the left side, choose Email-Addresses. On the right side, choose Name ID. Should look like the screen shot below:
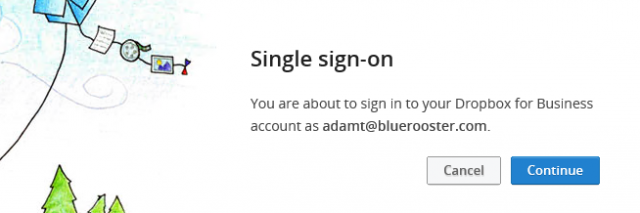
Step 4 – Try it out
Now that everything is setup, go to www.dropbox.com to try it out. When in optional SSO mode, you can use SSO if you enter your company email address, and leave the password box blank. This will tell Dropbox that you want to use SSO, and will redirect you to your ADFS servers for authentication. After being prompted for authentication, you’ll get taken back to Dropbox, where if everything went well, you’ll see the lovely screen below:















Hi Adam, great post! There’s virtually nil on dropbox/ADFS and this laid out the steps nicely.
I got everything configured and when i click the Continue button, i get this error on top of the page: Could not validate SAML assertion. Contact your team admin.
Any ideas where i can start with this error? TIA
I would suggest making sure you exported the correct token signing certificate, and changed the format to PEM. Also, make sure you have the claims attributes mapped correctly.
Great write up and it was a ton of help when I setup Dropbox with ADFS! Can I ask if you ever got the desktop client to work? I can use SSO on the web site with no issues but the dropbox desktop client wants to send you to get a link code (https://www.dropbox.com/help/1925/en). The desktop app takes you to the SSO portal during this process but then just signs you into the account without ever presenting a link code. So far dropbox support hasn’t been any help. I’m hoping you have run into this issue and resolved it.
I tried these instructions but kept having intermittent HTTP 500 errors/issues when signing in. When I contacted Dropbox support they said that their SSO does not support ADFS, and directed me to their SSO partners. This was in February 2014, so hopefully they will add official ADFS support soon.
Wait.. are you telling us that this whole SSO is ONLY for the Dropbox web login? So the binary client application for the various OSes does NOT work with SSO? The iPhone app; the windows client; the Ubuntu client all will not work via SSO?
Tell me I am wrong with that assumption?